IBM Released Its 2018 Data Breach Study — and Financial Services and Healthcare Organizations are Taking Note to Maintain Customer Trust
IBM and Ponemon’s latest Cost of a Data Breach Report illustrates the dauntingly true cost of a data breach to an organization, from direct financial impact to reputational damage and churn. Below is a breakdown of the 2018 IBM Data Breach study and a path forward for organizations to secure their business and enable customer trust.
Brief Overview
The study pinpoints the average total cost of a data breach at $3.86 million, which is a 6.4 percent increase over last year’s estimate. This year, the report also examined the costs of a “mega breach.” The average cost of a breach involving 1 million records is $40 million, while those involving 50 million records or more can cost a hefty $350 million. Notable mega breaches include Target, Equifax, Yahoo, and Uber.
The report is based off findings across 2,200 IT, data protection, and compliance professionals from 477 companies that have experienced a data breach in the past 12 months.

What Factors Affect the Cost of a Data Breach?
Calculating the true cost of a data breach to an organization is more complex than one may assume. This study found that the cost of data breaches has been steadily increasing over time — and has a hefty impact on a business’s bottom line. Factors that were found to affect the cost of a data breach include:
- Customer churn
- Number of records lost or stolen
- Time it takes to identify and contain a data breach
- Cost management
- Management of post data breach costs
Often people assume the cost of a data breach is analogous to the cost per record stolen, but it’s clear that the true cost spans far beyond the actual data stolen and can span far beyond the time frame in which the breach occurred.
How is the Cost of a Data Breach Calculated?
IBM’s report uses the activity base costing (ABC) methodology to accurately calculate the cost of a data breach. Four process related activities are factored into the cost of a data breach:
- #1 Detection and Escalation: Activities that allow a company to detect and report the breach to appropriate personnel within a specified time period (e.g., forensic investigation activities, audit services, crisis team management, communications).
- #2 Notification Costs: Activities that allow the company to notify individuals who had data compromised in the breach (e.g., newsletters, telephone calls, emails).
- #3 Post-Data Breach Response: Processes that help affected individuals or customers communicate with the company and costs associated with redress and reparation with data subject regulators (e.g., legal expenditures, credit reporting, issuing new accounts).
- #4 Lost Business Cost: Activities associated with the cost of lost business, including customer churn, business disruption, and system downtime (e.g., cost of business disruption, cost of lost customers, reputational loss).
The activities taking place both before and after a breach factor will heavily influence the cost of a data breach. And the systems, processes, and people your organization has in place will ultimately determine how severely your company will be affected by a breach.
What Industries Incur the Highest Cost for a Data Breach?
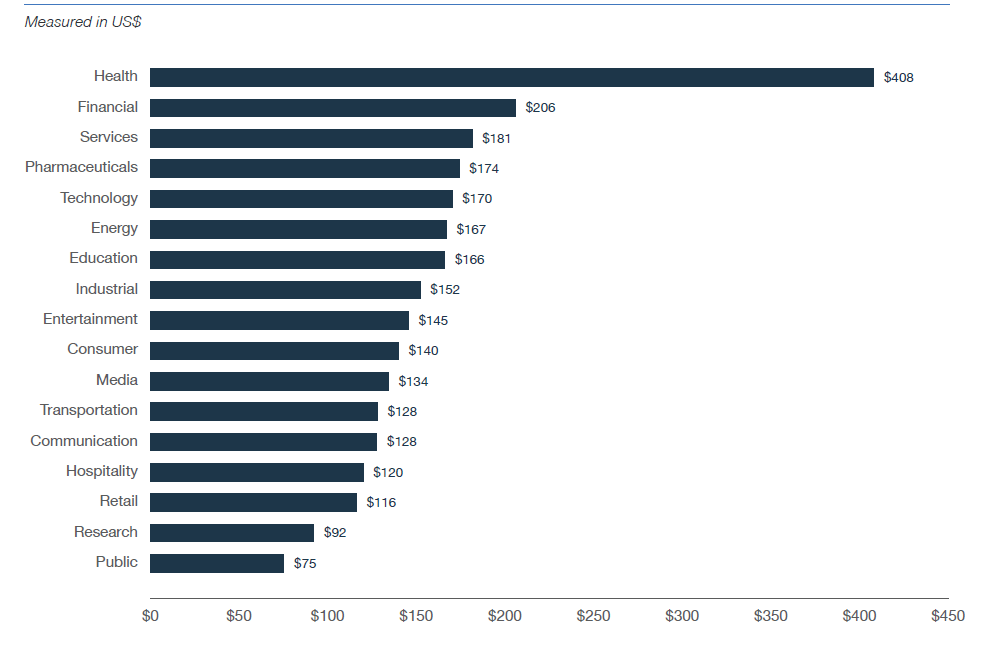
Highly regulated industries, such as healthcare and financial services, have the highest cost-per-record-breached among 17 industries. Healthcare records come in at $408 — 2.5 times the global average. Financial services takes second place, at $206 per record, or 29 percent more than the global average.
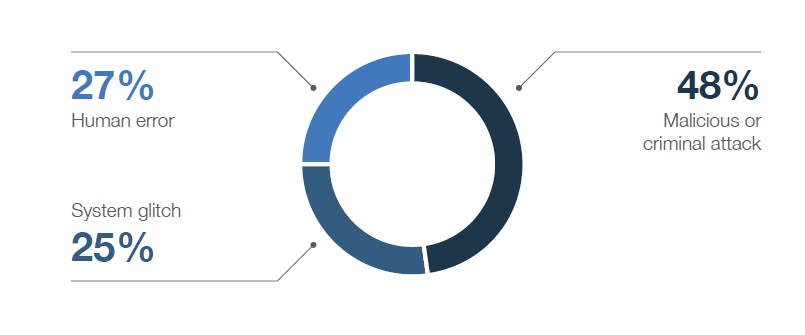
What are the Root Causes of a Data Breach?
Malicious and criminal attacks account for 48 percent of data breaches. Twenty-seven percent are due to negligent employees and contractors, and 25 percent involved system glitches, including both IT and business process failures.
Malicious attacks not only account for the majority of types of incidents, but they are also the most costly types of breaches. The cost per capita of a malicious or criminal attack is $157 — higher than the $131 associated with system glitches and $128 with human error.
Does Speed to Identify a Data Breach Affect Cost?
For the fourth year in a row, the study reports on the relationship between the financial consequences of a breach and the company’s speed of spotting and containing the breach.
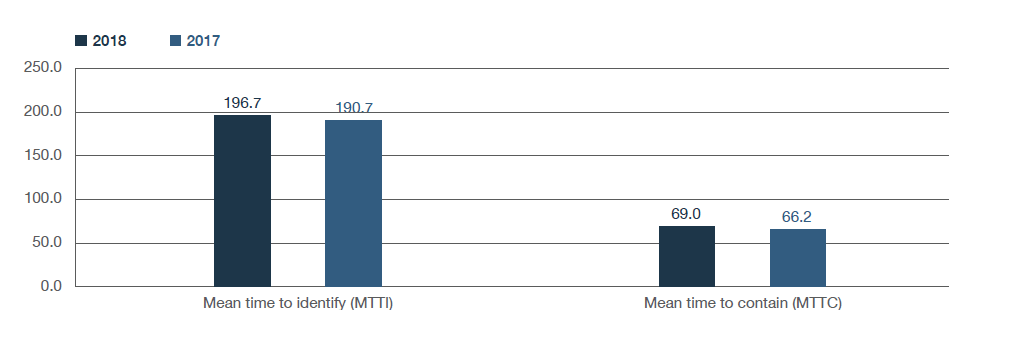
The mean time to identify a data breach is 197 days, while the mean time to contain the breach was 69 days. Breaches associated with malicious or criminal attacks take the most time to identify and contain, at 302 days. Glitch-related breaches take an average of 237 days, while human error breaches take around 231 days.
The financial impact of such a large gap is clear: For companies that contained the breach in less than 30 days, the average breach was estimated at $3.09 million, while a 30-day+ containment timeframe boosted costs to $4.25 million.
The significant cost difference between these two subsamples suggests that tools designed to improve detection or forensic capabilities can reduce the bottom-line impact of a data breach.
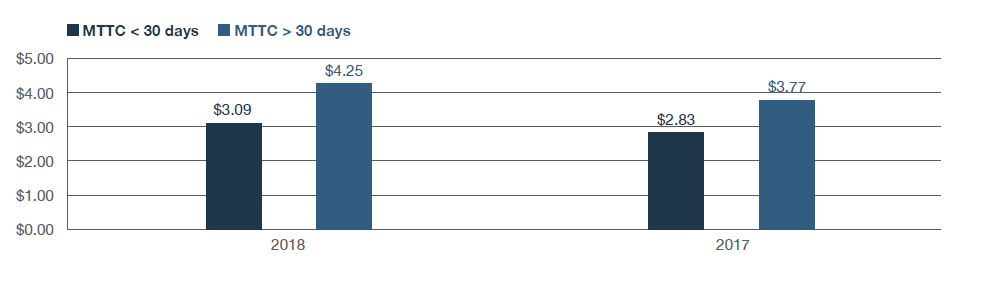
What is the Cost of a Mega Breach?
For the first time ever, the report also measured the cost of a mega-breach – a breach involving 1 million or more compromised records. The findings are based off 11 companies that have experienced a mega breach.
There are multiple cost components of a mega-breach: number of breached records, detection and escalation, notification, post-data breach response, and lost business. The study found that a data breach involving 1 million records costs around $40 million, while a breach with 50 million records costs around $350 million.
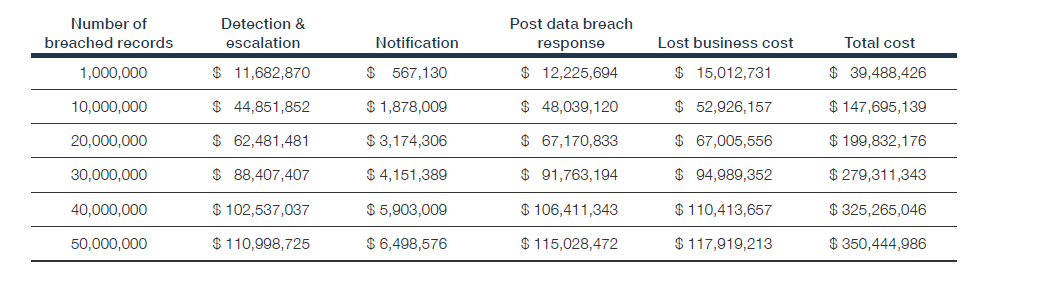
For organizations like healthcare and financial services, the reality of a mega-breach is more real than one may think. As large amounts of data/records are collected to enhance business processes and improve patient/customer care, this means a vast amount of data is also stored by the organizations. If not properly secured, businsses and care providers can be exposed to security incidents and breaches.
Breach Prevention in the 2018 Threat Landscape
Securing company data in the 2018 threat landscape is a complex challenge. Data are now widely dispersed as systems are rapidly becoming digitized, and the high value of data makes your organization an attractive target of malicious attacks. The IBM/Ponemon report shows that the more quickly businesses can identify and contain a data breach, the less financial impact there will be on the organization. And since 60 percent of data breaches are caused by insiders, this type of approach may mean securing your organization from the inside out.
Here are five steps organizations can take to reduce their risk of a data breach and empower their workforce:
Step #1: Assess what data your organization needs to protect most: Your organization most likely uses multiple applications, third-party partners, and an expansive workflow. This reality means that your data are probably not contained within a few secured systems. Take the time to conduct a comprehensive risk assessment to determine where to focus your security strategy. By knowing where your data is located and who has access to it, you’ll be better able to lay a foundation for additional security tools and data protection strategies. Questions include:
- What sensitive data does my organization store, use, and transmit?
- Who has access to what data?
- Who controls database access?
- Is my data secure when it’s not in use?
- Is my data secure in transit?
- What regulations/laws do I need to comply with (e.g., FINRA, HIPAA, PCI, FFIEC, NY State Cybersecurity Rule, GDPR, FCA, the California consumer privacy act)?
Step #2: Consider monitoring and behavioral analytics: Since detection time is one of the major factors in the cost of a breach, you should predict and prevent breaches by monitoring who is accessing your data and what they are doing with it. With the growth of electronic health records and cloud-based applications, company data is becoming centralized within a business network, making it potentially more easily accessible. To defend against internal threats, organizations can monitor user activity and utilize behavior analytics that provides insights into the who, where, when, and what of insider access. With better visibility into your business-critical applications, your security team can proactively detect, investigate, and isolate security incidents. Monitoring technology can also help enable trust in your employees by verifying that they are not putting your organization at risk by violating your acceptable use policies.
Step #3: Policies and procedures: Protecting company data is every employee’s responsibility. Create a transparent and explicit data security policy to help keep employees accountable and involved in security. Essential topics to consider for your policies and procedures include:
- Data privacy: Make sure your employees are fully aware of the laws they must comply with when handling your organization’s or customer’s data.
- Email usage: The majority of cyberattacks originate from email: In a study of 150,000 phishing emails by Verizon, 30 percent of recipients opened the infected messages, and a staggering 11 percent opened the attachments. To keep your company safe, make sure that your employees are trained on how to thwart social engineering.
- Password protection: Sixty-three percent of confirmed data breaches involve the use of weak, default, or stolen passwords. Maintaining strong password protection across your internal systems, then, can help prevent breaches.
- Mobile devices: It’s a world gone digital. Creating a mobile device policy that requires employees to password protection and secure usage will reduce risk of a data breach through unauthorized users and insiders.
Step #4: Maintain perimeter security and firewalls/patches: Maintaining proper perimeter security, including firewalls and patches are essential to securing your network. Not only should your security team be aware of the latest updated patches and potential vulnerabilities in your network, they should also implement the latest perimeter security and firewall technologies to thwart increasingly sophisticated cyber-attacks.
Step #5: Encrypt portable devices: While mobile devices have enabled meaningful collaboration and the interoperability of information, they can pose a serious threat to the security of a healthcare organization. To ensure security and compliance, proper security protocols must be put into place too. Consolidate data onto a secure cloud or data center behind a firewall to ensure you have oversight of company data.
Step #6: Prepare your incident response plan: Since detection and response time heavily contributes to the cost of a data breach, you should always be ready for the worst-case scenario. Craft a quality incident response plan (IRP) to help contain security incidents that would otherwise become full-blown breaches involving regulatory authorities. Once created, an IRP may frequent evaluation and changes as the organization naturally changes and evolves.
The cost of a data breach will continue to rise as cyberattackers and insiders leverage more sophisticated tactics to obtain data. In order to predict, prevent, and reduce costs the of security-related incidents and breaches, healthcare and financial services organizations in particular need to secure their organization from the inside out – and create an environment where employees are your greatest security asset, rather than your greatest vulnerability. In doing so, you can ensure that you enable trust between business and customer.
