Securing Your Sensitive Information in Salesforce: Data Protection and Security for Cloud

Businesses that rely on Salesforce for mission-critical activities generally store sensitive data in a CRM environment – financial records, PII, intellectual property, etc. But many users have access to that data, leaving it vulnerable to security risks. Protecting that information is critical in preventing data from being breached or landing in the hands of a competitor. To learn more about how to secure your sensitive information in Salesforce and why data protection and security are so important for the cloud, read on.
When it comes to your organization’s most sensitive data, you should know who is accessing what information in your critical applications to keep valuable company data inside the organization. Insider threats like disgruntled employees pose the greatest risk. According to The Ponemon Institute, the average annual cost of an insider threat is $8.76 million. In fact, 60% of all cybersecurity attacks are caused by employees inside an organization, with 44.5% being malicious insiders and 15.5% being inadvertent actors.
Organizations need to understand what causes insider threats in order to detect them and prevent consequences like a data breach, loss of trust, or millions in remediation costs. Depending on the industry and size of company, the cost of an insider threat varies dramatically. Highly regulated industries like financial services and healthcare see a much higher impact from insider threats due to the sensitivity of the data as well as regulatory penalties.
With user activity monitoring, you can gain insight into your employee’s behavior inside your cloud applications. In Salesforce, for example, you can detect suspicious activity like one user’s abnormally high number of exports or multiple failed logins from a particular IP address.
User activity monitoring: Exporting activity
Whether it’s a departing employee looking to take your data to a competitor or a careless employee frivolously exporting sensitive customer information, organizations must monitor for exporting activity within Salesforce. With the right solution, you can not only gain insight into who’s exporting data, but also who is running and viewing those reports.
Example: Keith, a long-time sales executive at your organization, has resigned. He says there’s no malice, it’s just time for him to move on. Using user activity monitoring to look back into his exporting activity, it seems Keith began exporting large amounts of customer information about three months before resigning. Before Keith can take this information to a competitor, you can address the situation and establish data protection and security without taking legal action.
User activity monitoring: Login activity
Application login activity can reveal valuable security insights. You may find out that employees are having trouble logging into Salesforce or there’s an abnormal login from an unknown location. With this information, you can confront and correct the issue before any serious consequences occur.
Example: Imagine your company is located in San Francisco, California. Your team travels the globe, but mostly in the continental United States and the U.K. One day, you get an alert that someone is trying to login from Moscow, Russia. No one in your organization is in Russia to your knowledge, and this seems suspicious, so you shut down the login and thwart a potential threat while you investigate the unusual activity. It turns out that Sarah, Director of Client Relations, was traveling in the U.K. when someone stole her laptop at the airport. Since she boarded the flight using her mobile phone, she was unaware that her laptop was missing. She only realized what happened when your team contacted her regarding suspicious activity on her Salesforce account. Luckily, the activity was shut down immediately upon detection.
Read a true story about login activity and its implications for your business as a potential threat here.
A look into the future: User behavioral analytics
“To predict future behavior, look to past behavior” is a useful maxim in almost all areas of life, but it’s especially pertinent for internal monitoring. Abnormal activity in Salesforce can provide invaluable insights into an employee’s probable behavior.
Example: Tim, an Account Manager, accesses around 100 accounts per day in his usual work activity. Suddenly, he starts accessing over 300 accounts per day. Digging into analytics, you can see what drove this behavior. Was it business related or does it seem like suspicious activity? With behavioral analytics, you can observe and make an appropriate judgment, putting a stop to potential data theft. Drawing valuable insights from Tim’s past behavior, you conclude that he was working after hours and increased his prospecting performance. You’re able to identify the activity as business related and save valuable time that a manual investigation would have required.
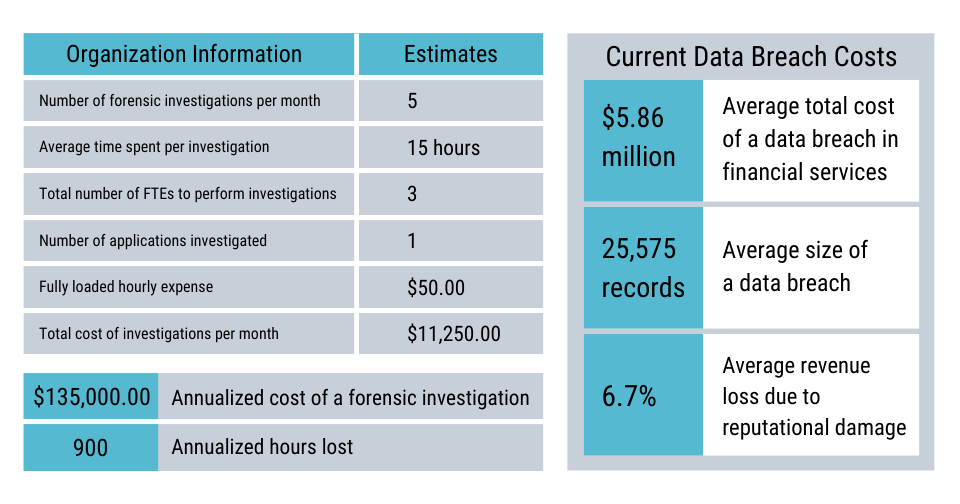
Cost to your organization
The cost of forensic investigations and data breaches to your organization may be far higher than you would expect. Calculate the cost of your investigations per month using a chart like the one below:
Rapid regulatory reporting for cloud compliance
We exist in an era where cybersecurity threats are present anytime, anywhere. Data protection and security are more important than ever, as evidenced by widescale ransomware attacks like WannaCry, SamSam, and SimpleLocker. These threats to sensitive information are not going unnoticed – and usually involve an insider threat. Regulatory bodies and regulations are sprouting at a record pace in countries and territories around the globe to ensure that organizations secure consumers’ personal information. Organizations are capturing the power of cloud technologies such as Salesforce Shield: Event Monitoring to take control of their data and bolster security measures to comply with these government regulations.
