Healthcare Data Security Breaches: Singapore’s Historically Large Data Breach Committed by Highly Sophisticated Cyber-Criminals

This week, Singapore announced a data breach at its largest healthcare provider, SingHealth; among its victims were Prime Minister Lee Hsien Loong. This instance is just one example of many widescale healthcare data security breaches in the recent past, with over 30 major healthcare data breaches reported in 2018 in the U.S. alone.
The official press release notes that the data of about 1.5 million patients visiting SingHealth’s specialist outpatient clinics and polyclinics between May 1, 2015, and July 4, 2018, were illegally accessed and copied. Information was also exfiltrated on the outpatient dispensed medicines of about 160,000 of these patients.
The High Value of Healthcare Data Drives Criminals and Insiders to Go the Extra Mile
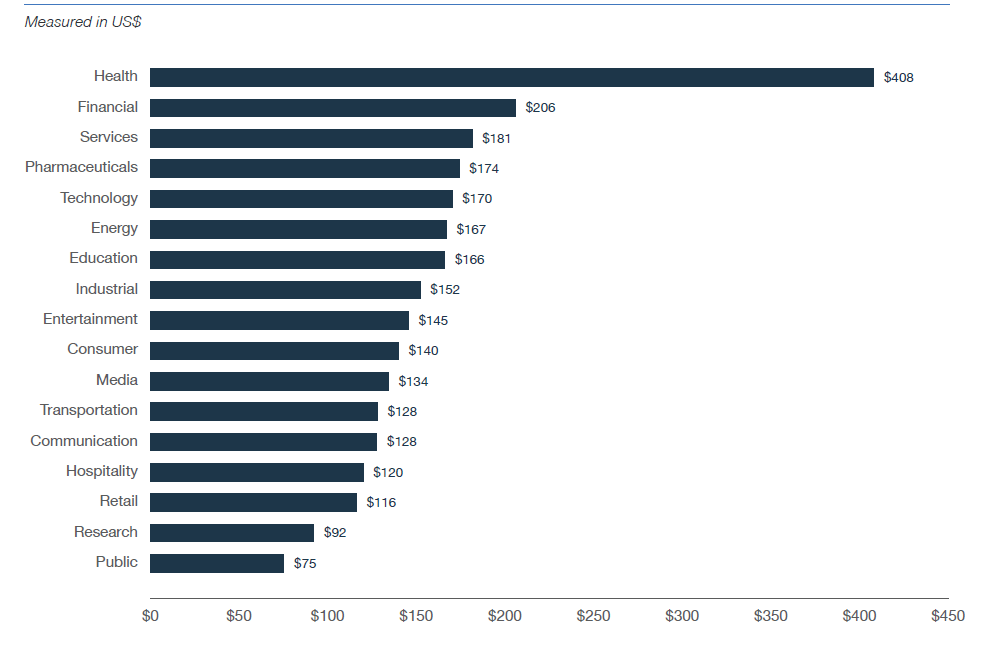
So what’s driving this influx of malicious healthcare data security breaches? The new reality is that healthcare data have become so valuable ($408 per record) that hackers, attackers, and insiders may be willing to go the extra mile to obtain it, according to the IBM 2018 Cost of a Data Breach Study. As shown below, highly regulated industries such as financial services and healthcare have the highest value-per-record out of 17 major industries.
Healthcare Data Security Breaches Driven by Malicious Attacks
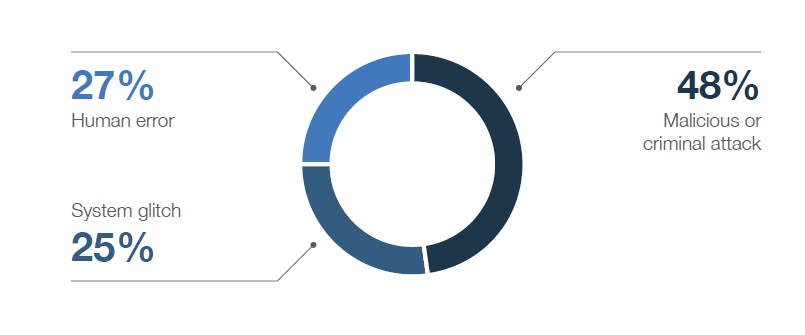
Healthcare data security breaches can be caused inadvertently or purposefully, by hackers or insider threats. Malicious and criminal attacks now account for a majority of data breaches at 48 percent (according to IBM). Twenty-seven percent are attributed to negligent employees or contractors, and 25 percent involved system glitches, including both IT and business process failures. Malicious or criminal attackers seek patient data to engage in drug diversion, identity theft, fraud, espionage, and more. Most recently in the U.S., the largest ever national healthcare fraud takedown in history was announced. In the drug diversion-related case, the U.S. Department of Justice and the Department of Health and Human Services (HHS) announced 601 charged defendants — a clear signal of a no-nonsense stance toward healthcare security breaches.
And while 48 percent of data breaches are malicious and criminal by design, 58 percent of breaches also involve insiders, according to the Verizon 2018 Protected Health Information Data Breach Report. This highlights the fact that organizations can no longer rely on a “mote mentality” of perimeter security. Whether the data breaches are carried out by outsiders or insiders, the fact remains that the majority of data breaches are enabled by an insider. Outside attackers use social engineering to compromise user credentials and gain access to the care providers network in order to gain access to patient data.
Adopting an Inside-Out Approach to Privacy and Security in the Age of Advanced Threats
So what can healthcare organizations do to prevent healthcare data security breaches associated with malicious attackers and insider threats? It starts by creating a foundation of patient data privacy and security for your care program. Healthcare providers can take the following steps:
- Conduct a risk analysis of all systems holding ePHI. Risk analysis looks at where your ePHI is stored and prioritizes the systems holding ePHI. Under the HIPAA Security Rule, all applications containing PHI are subject to the HIPAA Laws. Conduct a risk analysis to identify all systems and applications that contain ePHI and better monitor patient information.
- Strengthen identities and monitor activity to predict and prevent breaches. Healthcare organizations can use behavioral analytics and auditing to ensure the safety of mission-critical applications and systems. Since 58 percent of security incidents are caused by insiders, make sure to monitor user activity within EHRs and cloud applications to detect suspicious or unusual behavior. The quicker you can spot a breach or security incident, the faster it can be contained and mitigated – especially since the average time to detect a data breach is 206 days. A patient privacy monitoring platform can help you keep an eye on access and activity across applications.
- Regularly review access rights management. Since malicious hackers and insiders often seek privileged credentials to help them carry out their attacks, users should be monitored to identify permissions that can be rolled back or reduced. Users should be given permissions only to what is necessary to perform their job role. Organizations can customize privileges for each user and application. If an employee needs read/write privileges to a certain file system, for example, then they don’t necessarily need root privileges. Applying unnecessary privileges puts your organization at increased risk.
- Employ managed security services. Healthcare organizations need to strengthen their privacy and security stance in today’s landscape of increasing threats. However, industry challenges such as staff turnover, scale, budget, and complex workflows make it difficult to hire and retain cybersecurity staff. Managed privacy services (MPS) can help strengthen healthcare privacy and security teams, providing outsourced monitoring and helping manage accounts, devices, and systems. In many cases, MPS can reduce workload by up to 80 percent.
- Drive culture and training. Any organization handling PHI should be driven by a clearly defined culture of privacy and security. Users should be trained to identify and thwart phishing attacks that could infiltrate the organization and spread ransomware. Also, train users on acceptable use policies and procedures through an LMS to boost compliance.
- Prepare an incident response plan. You should always be ready for the worst-case scenario. Crafting a quality incident response plan (IRP) will help contain security incidents that would otherwise become breaches with regulatory involvement. Under the HIPAA Security Rule, all covered entities require an IRP. The HHS provides a free incident response plan template to help organizations craft an agile plan for handling incidents.
To secure patient data in the age of advanced threats, including external and internal attackers, you must take a multifaceted approach to data security. As new technologies are adopted to improve patient care, organizations should have an explicit understanding of how and where patient data is stored, transmitted, and secured. Creating a foundation of patient data privacy and security where information is secured from the inside out will allow care providers to focus on improving patient care.
Learn more about securing patient data with Imprivata FairWarning’s Imprivata FairWarning Patient Privacy Intelligence platform.
