What to Monitor in the Cloud: 2018 Cloud Visibility Report Reveals Blueprint to Success

Cloud spending is forecasted to reach $160 billion in 2018 – a 23.2 percent increase over 2017. Businesses around the globe are capturing the benefits of cloud technology to meet consumer demand in today’s fast-paced ecosystem. But without insights into users’ activity in the cloud, organizations can be left vulnerable to data breaches, insider threats, wasted resources, and decreased customer trust. The question becomes what to monitor in the cloud.
Many organizations have begun looking for ways to monitor how users are interacting with cloud applications and customer data – using the audit logs (e.g., Salesforce Shield Event Monitoring) available in many cloud applications. And for financial services companies, healthcare organizations, and others in highly regulated industries, monitoring is becoming an even more essential part of the culture as countless regulations and security frameworks (e.g., the California data protection law) set a foundation for monitoring systems that hold sensitive data.
By examining the events documented by your applications’ audit logs, you can gain deep insights into:
- Are departing employees exporting sensitive data?
- Are inactive users trying to log in?
- Who logged in this week (and who did not)?
- What customers are experiencing Community login failures?
- What were the top Visualforce pages accessed, and by whom?
- What is the trend of successful vs. failed logins?
- What permission sets have been created, assigned, or unassigned?
- Who has escalated privileges?
- What permissions and profiles have been changed?
But where to start? The 2018 Cloud Visibility report analyzed more than 1,200 monitored policies of Imprivata FairWarning customers monitoring more than 18,000 users with the Imprivata FairWarning for Cloud Security platform. The results reveal the priorities of organizations that are already monitoring – and gives a glimpse of what’s possible when seeking greater visibility in cloud applications.
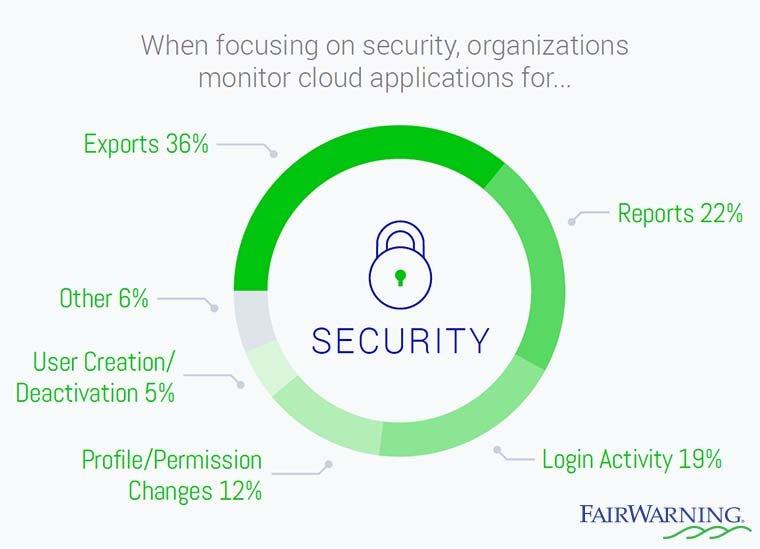
What to Monitor in the Cloud for Security: Exports and Reports Can Reveal Exfiltration
As organizations’ tech stacks continue to grow in the cloud, the human attack surface becomes broader. With applications like Salesforce and Dropbox, valuable internal and customer data suddenly becomes available 24/7, anytime, anywhere. Security controls can help manage who is logging in and when, but what if those security controls were accidentally changed? Credentials may be tightly managed, but what if a customer were conned into providing their Salesforce Community login information to a bad actor? For those without visibility into the basic handling of sensitive data within their cloud applications, every user can start to look like a potential threat.
A lack of security can also impact an organization’s growth and innovation, making it more difficult to meet workforce and customer needs. According to McAfee, 40 percent of businesses are delaying cloud adoption because of a perceived lack of cybersecurity skills. This gap can leave companies vulnerable – and business systems and applications like Salesforce should not go unmonitored.
This gap can leave companies vulnerable – and business systems and applications like Salesforce should not go unmonitored. Exports and reports are the first area companies are turning to, with 58 percent of security-related monitoring policies centered around these two areas.
“If you have somebody who, over the last three years, has been looking at 20 records per week, and suddenly they decide to download 3,400 records, that is an export over average,” said Mark Bowling, United Capital’s Consulting ISO on the webinar “5 Strategies for Preventing Privileged User Abuse in Salesforce.” “And then we have to ask the question: ‘Why did they export 3,400 customer records? Do they really need to look at 3,400 customer records? And is that a potential indication of misconduct?”
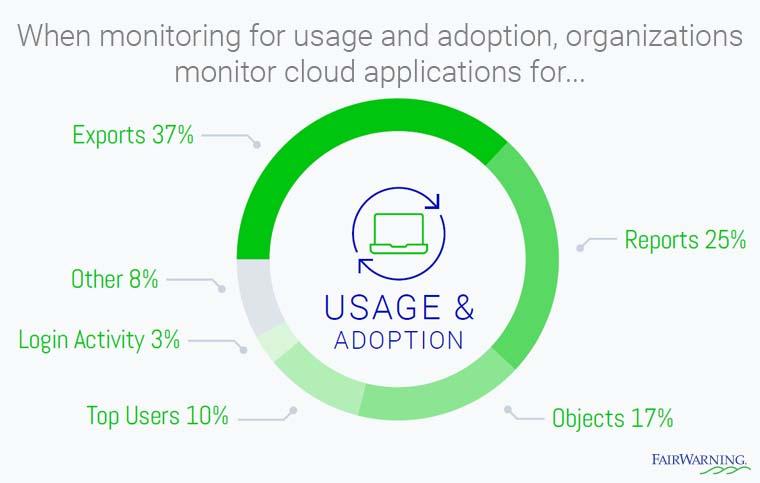
What to Monitor in the Cloud for Usage & Adoption: Exports, Reports, and Object Activity Are Chief Areas of Concern
Once companies begin monitoring for security, they often begin monitoring for additional areas, like usage and adoption. Applications like Salesforce can be very costly for organizations, so it’s essential to make sure your investment is providing a return. And one of the best ways to do so is by looking at who’s using the application, and how.
Cloud application usage can have a direct impact on your bottom line: The Harvard Business Review reported that over half (52 percent) of top sales representatives say they’re CRM “power users,” leveraging their organization’s technology and systems to their fullest. This stands in contrast to the 31 percent of underperforming sales reps who said the same. So how can you capture the success of top performers and scale that across the company? It starts with getting a picture of exactly what those top performers are doing in the CRM and other systems.
“In my role, I need to make sure what we are building is used by the business,” said Starwood Capital Group project manager and solution architect David Tebbi. “Having the ability to track usage and the flow of data among users has reassured management that our investment in Salesforce has been worthwhile.”
When turning to usage and adoption are first monitoring exports and reports to measure usage of Salesforce and other cloud applications. While these two areas can also reveal security vulnerabilities, they may also reveal training opportunities. For instance, an export of a large report may not indicate an employee is stealing data. It could be, instead, that users aren’t able to properly run reports or filter for relevant criteria, so they’re repeatedly exporting large reports and still not finding the information they need. Personal and unsaved reports might also be an indication that users aren’t sure how to best use the program for their needs.
With advanced insights, you can ensure trust in your cloud applications by answering key compliance questions like:
- What reports are top performers running?
- What objects are users accessing, and can that be correlated with greater success in their role?
- Who are your top users?
- Who’s logging in (and who’s not?)
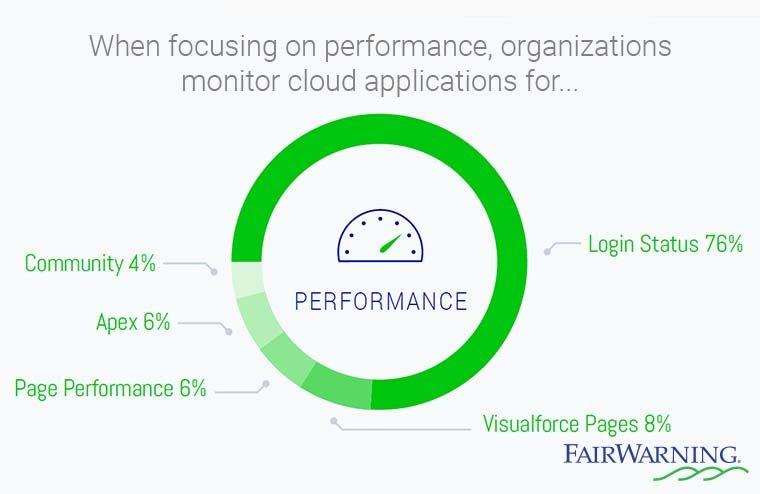
What to Monitor in the Cloud for Performance: What Logins are Succeeding (or Failing?)
The performance of your Salesforce and other cloud applications is directly tied to your business’s productivity and ROI. Performance broadly refers to the metrics and availability of information within your Salesforce application, and thus the end user experience. Without insight into how your cloud applications are performing, users could end up creating workarounds that waste time and undermine usage, adoption, and trust in your application. This is true whether it be internal or community users.
Monitoring Salesforce application performance provides you the insights needed to increase application productivity and, therefore, the productivity of users (e.g., sales representatives, developers, HR, finance, community users). This is essential when each moment wasted can be linked directly to your bottom line.
With advanced insights into performance, you can take a proactive approach to maximizing workforce productivity and enabling trust between yourself, your users, and your customers. You can also save time when investigating the source of performance discrepancies – and point your developers toward the root of the problem, even providing justification for Salesforce development spend – by asking questions like:
- Which users are receiving login failures?
- What were the top Visualforce dashboards accessed?
- Which pages have failed?
- Why are Community login failures happening?
- What is the trend of successful vs. failed logins?
- What Apex execution events occurred (by user or day)?
“We’ve been able to measure the performance of our Salesforce system,” said Thomson Reuters Head of CRM and Business Information Andy Louca. “What we found is a number of Visualforce pages are poor performing — or failing entirely, in some cases. Knowing that, we could focus on fixing those and creating a better user experience.”
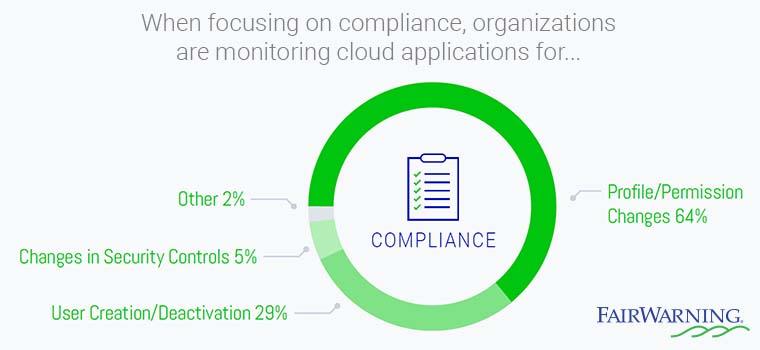
What to Monitor in the Cloud for Compliance: Permissions and Users Big Areas for Regulations
As organizations shift to the cloud, they have also found new and more efficient ways to meet compliance requirements and security frameworks. Many cloud-based technologies have beefed up security features that can help meet regulations and, thus, allow highly regulated industries to entrust their data to the cloud.
Yet a major cloud compliance misconception is that your application provider is solely responsible for the security and compliance of your data storage and handling. Instead, it’s a shared responsibility. Compounding the responsibility is the number of existing regulations, as well as the new ones sprouting up at record pace. In addition to the regulations from FINRA, HIPAA, PCI, FFIEC, and FCA, new regulations include the EU’s General Data Protection Regulation (GDPR) and the New York State Cybersecurity Rule. In addition, all 50 states in the U.S. now have individual data regulations in place, further complicating the landscape and making it important to approach cloud application compliance holistically.
GDPR is perhaps the most significant new regulation, in that it affects the way organizations collect, store, and transmit EU citizen data. Fines can equal 4 percent of annual turnover, or 20 million Euros, making noncompliance a bottom line-breaking event.
Now, more than ever, organizations must put in place controls to maintain an overarching view of their data. By monitoring for events, you’ll be armed to answer key questions about how users are handling sensitive data and security controls. And in doing so, you can better harness the power of cloud data security, paving the road to cloud compliance.
“It’s been nice to have our compliance and sales teams working together to make sure we’re doing everything we need to do to secure our Salesforce data,” said Jefferson National’s Director of Territory Consultants Amy Mattingly.
With advanced insights, you can ensure trust in your cloud applications by answering key compliance questions like:
- What permission sets and profiles have been changed?
- What profiles have been created?
- What users were created or deactivated?
- What IP whitelists were updated?
