5 Types of Insider Threats in Healthcare – and How to Mitigate Them

Cybersecurity threats are happening constantly in healthcare – last year, a new breach was reported every day. From phishing attacks to malicious insiders, all sides can be left vulnerable. But the insider threat can be one of the most damaging to healthcare organizations – according to the 2019 Verizon Insider Threat Report, 46 percent of healthcare organizations were affected by insider threats. In fact, it was the only industry where insiders were responsible for a higher percentage of breaches than external actors. So what are the types of insider threats in healthcare, and how can you quickly identify them and mitigate their risk?
Insider threats are defined by The Verizon Insider Threat Report as those “originating from within the organization… full-time (or part-time) employees, independent contractors, interns, and other staff.”
These insiders can be just as – if not more – dangerous than outside actors. This is because insiders have added advantages that aren’t available to outsiders such as security access, organizational trust, and knowledge of procedures.
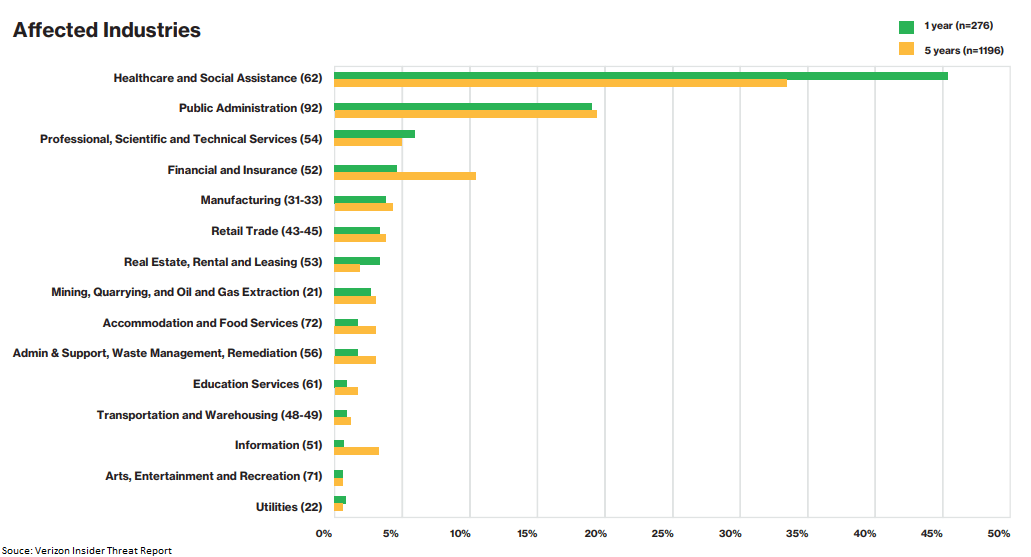
The most alarming part? When a breach occurs, it’s rarely discovered quickly. On average, it takes about 350 days to identify and contain a data breach in the healthcare industry. Furthermore, the medical field falls victim to data breaches more than any other industry at an alarming rate of 44.9 percent. Since insiders may repeatedly violate policy – particularly if they fall in the “careless worker” category rather than a malicious actor – that means you may have repeated incidents until you’re able to uncover them.
What should you look for to prevent potential breaches from happening from within your organization? Here are five common inside sources and how to mitigate them.
1. The Careless Worker
The Careless Worker may be perfectly well-meaning, but when they bypass security and privacy measures, it creates massive privacy and legal implications. In 2018, healthcare organizations paid a record-breaking $28 million in financial penalties to the Office for Civil Rights (OCR) in response to HIPAA violations. When employees break acceptable use policies, leave sensitive PHI in plain sight of onlookers, or install unapproved applications onto company devices, they leave their network vulnerable to infiltration.
Careless Workers are usually unaware that they’re committing HIPAA violations – or your facility may lack a “culture of privacy,” leaving the door open to Careless Workers to snoop on coworker or neighbor records or violate internal policy by self-accessing their own records “because everybody else does it.” In these cases, though, negligence can be just as dangerous as malicious intent.
To prevent the Careless Worker from breaching patient data and putting your organization at risk, you can establish and reinforce guidelines from the point of hire. Have new hires sign an NDA followed by an onboarding process where both security measures and HIPAA compliance are clearly explained, and you can turn a potential Careless Worker to one empowered to avoid a breach. Patient privacy monitoring can also help you spot common trends in improper access and anomalous behaviors that can inform retraining and remediation efforts and create a culture of privacy.
2.The Inside Agent
The contract IT worker down the hall. The custodial staff. Ted from Accounting.
From third-party contractors to permanent staff, the Inside Agent could be anyone. According to the Insider Threat Report, an Inside Agent is an employee who has been coerced, recruited, or bribed into siphoning data from an organization and into a third party’s hands.
Fortunately, you can take measures to stop Inside Agents in their tracks. Per the HIPAA Security Rule, you can restrict file access to only authorized users or implement user activity monitoring to send alerts when suspicious activity is detected – helping you reduce the risk from Inside Agents right away.
3. The Feckless Third Party
Feckless Third Parties are typically business associates that compromise security through improper use, negligence, or harmful access. They can be especially dangerous, as business associate breaches leaked over 100,000 patient records in January 2019 alone.
To mitigate risks from Feckless Third Parties, always investigate hardware supply chains to confirm their positive reputation and trustworthiness. On top of that, you can install a system that monitors suspicious network traffic, unusual activity, and remote access. These measures, along with disabling any compromised user accounts, can prevent potential third-party attacks.
4. The Disgruntled Employee
Whether they’ve been let go for missing quotas or are looking to transition to another company, the Disgruntled Employee is a potential threat to watch for – it’s especially easy for them to feel as if they were treated unfairly. Disgruntled, in a financial bind, and tempted to leak PHI, they may seek to take private data out the door with them. They could also turn into an Inside Actor, vulnerable to criminal activity in their final days with the organization.
Fortunately, you can do plenty to protect data from a resentful employee. By monitoring for signs an employee is about to quit, setting up an action plan, and restricting controls before they’re let go, you can protect your healthcare organization from the insider threat of a departing employee.
5.The Malicious Insider
Malicious Insiders are one of the most challenging threats to detect. Unlike the Inside Actor, they typically act on their own motivations rather than those of an external party. They can leverage their privileges to access private information for personal or financial gain. And because they’re already inside the network, they have no roadblocks preventing them from abusing secure data. According to the Verizon Insider Threat Report:
“A malicious insider is a current or former employee, contractor, or business partner who meets these criteria: they have or once had authorized access to an organization’s network, system, or data; and they have intentionally exceeded or intentionally used that access to negatively affect the organization’s information.”
These are the types of people who would leak a patient’s personally identifiable information (PII) to identity thieves for profit, making it easy for patients to fall victim to financial fraud.
As difficult as it can be to detect Malicious Insiders, you can use countermeasures to protect sensitive data. These include controlling access so that only individuals with a “need to know” can log in, programming screen locks, monitoring users for suspicious activity, restricting the use of USB storage devices, and disabling access for any inappropriate activity.
The amount of risk within healthcare organizations is staggering, considering the valuable and personal data that is handled on a daily basis. Fortunately, insider threats can be reduced by taking a variety of measures: put a thorough HR process in place (including onboarding, disciplinary action, and exit processes), establish compliance training, implement HIPAA security measures like workstation locks, and leverage user access monitoring, and you’ll be well on your way to protecting your organization from a potentially disastrous – and expensive – breach.
