5 Types of Insider Threats in Financial Organizations – and How to Mitigate Them
Cybersecurity threats are a continuous concern for financial organizations – in fact, financial service firms face 300 times more security incidents than other industries. Breaches can originate from both external and internal sources. Regardless of the cause, all sides can be left vulnerable. But insider threats in financial organizations can be one of the most damaging to financial organizations – according to the 2019 Verizon Insider Threat Report, about half of internal actors are motivated by financial reasons. In fact, Verizon’s findings demonstrate that financial motivation was by far the top driver for insider attacks.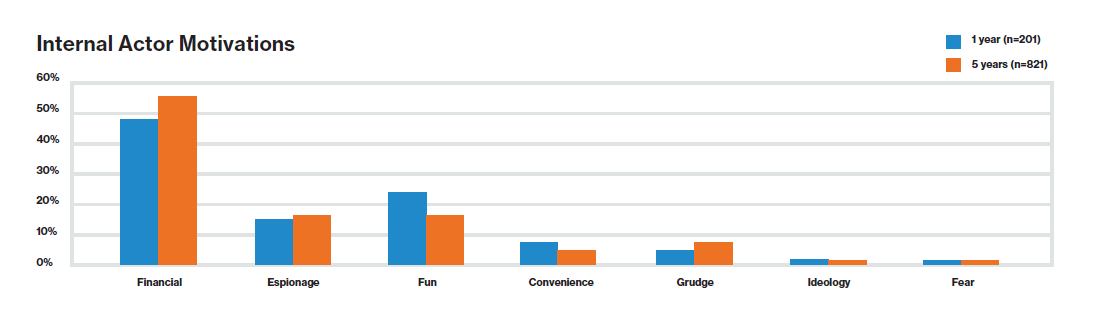
Source: 2019 Verizon Insider Threat Report
The Verizon Insider Threat Report defines insider threats as those “originating from within the organization… full-time (or part-time) employees, independent contractors, interns, and other staff.”
While most organizations focus on outside actors, insiders can be just as – if not more – dangerous. Insiders have advantages that outsiders don’t, like security access, knowledge of policies and procedures, and organizational trust.
What’s most alarming is it can take a long time to discover a breach: On average, malicious or criminal attacks take more than 300 days to identify and contain. And because insiders may repeatedly violate company policy (particularly if they’re an “oblivious worker” as opposed to a malicious actor), you may find that multiple incidents occurred before you discover even one.
How can you identify potential insider threats and prevent them from happening? Here are five common inside sources and how to mitigate them.
1. The Careless Worker
Careless Workers may not have malicious intentions, but mistakes and misuse of assets can still create serious security problems. In 2018, heavily regulated industries suffered the most when it came to per capita cost of a data breach; financial services stood out at $206 per capita. When employees break security policies, leaving computers logged into mission-critical systems like Salesforce or installing unapproved applications onto company devices, they leave the entire network vulnerable.
Careless Workers are usually unaware that they’re jeopardizing the security of the entire organization. However, negligence can be just as dangerous as malicious intent.
To prevent the Careless Worker from causing breaches and putting your organization at risk, you can establish and reinforce security guidelines, starting with the onboarding process. New hires can sign an NDA and complete training that covers security measures and regulation compliance. With the right education, you can turn a potential Careless Worker into one empowered to avoid a breach. User activity monitoring at the application level can also help you spot trends in privilege abuse and suspicious behaviors, which you can use to identify potential security incidents before they cause chaos.
2. The Inside Agent
The contract auditor down the hall. The janitorial staff. Jack from R&D.
From third-party contractors to full-time employees, the Inside Agent could be anyone. According to Verizon’s Insider Threat Report, Inside Agents usually act on behalf of a third-party external threat after being coerced or bribed into stealing data from an organization.
Fortunately, it’s possible to stop Inside Agents in their tracks. For financial institutions, you can restrict file access to authorized users only or implement user activity monitoring to send alerts when suspicious activity is detected – helping you reduce risk in near real-time. Plus, network security controls like user activity monitoring can help you meet financial regulation requirements like GLBA, PCI-DSS, and SOX.
3. The Feckless Third Party
Feckless Third Parties are threat actors that compromise organizational security through misuse, negligence, or malicious intent. They can be especially dangerous. Take the Equifax breach, for example – Equifax blamed the incident, in part, on flawed outside software, as well as a malicious download link from another vendor.
To alleviate the risk of the Feckless Third Party, regularly audit third-party vendors and supply chains to confirm their trustworthiness. Additionally, you can install monitoring systems that identify suspicious, unusual, or unauthorized network activity. These measures, along with disabling compromised accounts, can help prevent third-party attacks.
Source: 2019 Verizon Insider Threat Report
4. The Disgruntled Employee
Regardless of why they are departing the company, the Disgruntled Employee is another insider threat to monitor. They may feel they were treated unfairly and retaliate. Disgruntled and in a tight financial spot, they may be tempted to steal personal information or sensitive data on their way out. They could also become an Inside Actor during their final days with the organization, exporting information like customer or prospect lists and other IP as they prepare to depart.
Thankfully, you can protect your financial services organization’s network and data from indignant employees by implementing a monitoring program to detect potentially risky employees. Then, you can establish an action plan and restrict controls before they’re let go.
5. The Malicious Insider
It can be particularly challenging to detect Malicious Insiders. Unlike Inside Actors, Malicious Insiders are usually self-motivated, as opposed to incited by an external party. And with their privileges, they can access private information for personal or financial gain, often remaining undetected for some time. Many malicious insiders have network privileges that give them direct, unrestricted access to customers’ or the business’ sensitive financial information, which they may steal, destroy, or release. Other insiders may steal coworkers’ credentials to gain access to sensitive data.
These people can leak a customer’s personal banking information to criminals, steal identities, sell data on the dark web, or use it in other ways that can lead to chaos both for customers and your organization.
Though Malicious Insiders might fly under the radar, financial services organization can use countermeasures to help protect sensitive data. These include access controls like the principle of least privilege, workstation locks, user activity monitoring, restrictions on hardware such as USB drives, and disabling access upon detection of inappropriate activity.
Circumventing the Insider Threat in financial organizations
Financial organizations face a staggering amount of risk on a daily basis, and the amount of personal and business data stored in networks continues to expand. As such, the insider threat is a serious concern that’s only becoming more concerning as technology and tactics develop. Fortunately, measures exist that can stop insider threats in their tracks.
First, establish a thorough HR process that includes onboarding, disciplinary action, and exit processes. Next, implement ongoing compliance training programs to make sure everyone is up-to-date on the latest threats and can identify suspicious activities. After that, install security measures such as user activity monitoring and keycard door access as part of a defense-in-depth approach to security, and you’ll be off to a great start in protecting your organization from a potentially catastrophic – and costly – breach.
