The 6 Elements Every Financial Institution Needs for Defense-in-Depth Security

In the same way that medieval castles were designed with multiple security layers for protection, today’s organizations require a multifaceted approach to safeguarding highly sensitive data. Defense in depth security is critical for financial services storing sensitive data in cloud applications like Salesforce, Google Drive, or Office 365 because that data often includes PII like names, addresses, account numbers, and Social Security numbers.
Financial institutions succeed when customers can trust them to fervently safeguard their sensitive data. The best way to secure that data is to deploy multiple defensive measures, as no single option is completely infallible — if one security control fails or a hacker exploits a vulnerability, they could instantly access all the sensitive data stored in an application. Multiple barriers may seem redundant, but that’s the point – should one layer fail, numerous others are immediately at the ready to thwart any danger.
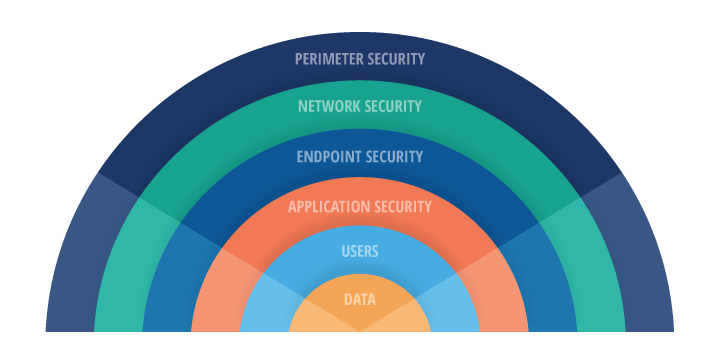
A defense in depth security strategy implements numerous layers of defense against threats, including:
- Administrative controls
- Physical barriers
- Perimeter security
- Network security
- Endpoint security
- Application security
The first two layers – administrative controls and physical barriers – are social and physical methods of defending data.
Administrative controls like policies, procedures, and training give employees the resources to identify potential threats and mitigate them whenever possible. For example, company policy may prohibit employees from removing documents from the building or require them to label all sensitive information as “confidential.”
Physical barriers like gated building access, key card access to offices, and laptop locks can physically block a hacker from gaining access to sensitive data.
The other defense-in-depth layers represent technological defenses. These are technical controls based on the network systems, devices, hardware, software, and other technology on which organizations rely. Each layer of the defense-in-depth approach increases security defenses exponentially, securing personally identifiable information (PII) and other confidential data.
Common security concerns that a defense-in-depth approach addresses
Organizations most commonly face three security concerns:
- The skilled attacker
- The insider threat
- A compromised system
A skilled attacker may be an individual or a group of hackers capable of successfully breaching security measures using any means necessary. Often, skilled attackers rely on social engineering tactics like calling a help desk or emailing an employee to obtain names, numbers, and other information that can help them cross security barriers. If threats break through the perimeter or network security, additional layers like endpoint or application security can stop them in their tracks.
The insider threat comes from within an organization – whether a current or former employee, the attacker has intimate knowledge of the inner workings of a company and uses that information to gain unauthorized access to data, often exporting large quantities of highly sensitive information. A defensive layer like application security with user activity monitoring can proactively alert admins to abnormal activity, preventing data loss and shattered trust.
Compromised systems raise the stakes a considerable amount – with access to just one computer on a network, an attacker can quickly break into an organization’s entire infrastructure. There, they can rapidly hijack and override other security measures, which is why numerous strategic defenses are key.
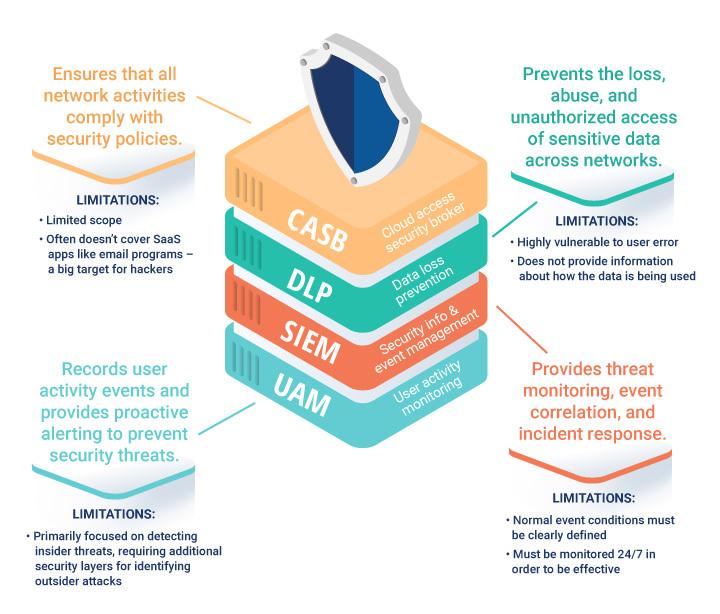
Technical cloud security controls
Finance, banking, insurance, and other industries storing PII or other highly sensitive data in cloud applications often rely on technical controls like CASB, DLP, and SIEM solutions. While these are all excellent options for building a security program, they are not enough on their own. Each has its limitations and vulnerabilities, but when combined with multiple other layers, they can support a nearly impenetrable security posture.
CASB
A cloud access security broker (CASB) tool acts as a gatekeeper between on-premises and cloud-based infrastructures. CASBs can provide insights into cloud usage and help detect shadow IT operations.
Yet the insights CASBs provide are limited in scope – many CASBs don’t cover SaaS applications like email programs, which are one of the biggest targets for hacking tactics like phishing. The 2018 Verizon Data Breach Report showed that 98 percent of social attacks consist of phishing and pretexting incidents, and email is the most common path of attack, making up 96 percent of incidents. To prevent an influx of scam attempts, other layers of defense, like a network firewall and endpoint security, are necessary.
As with SIEMs, user activity monitoring can be integrated with a CASB: CASBs can ingest event monitoring log data to detect potential threats and alert security teams before the threat escalates. By adding cloud access data and event logs, InfoSec teams can gain in-depth visibility into application activity like creating or deleting contacts, running reports, or exporting data in Salesforce.
DLP
Data loss prevention (DLP) solutions aim to address questions like:
- Where is sensitive data being stored?
- How is it being used?
- How can we prevent data loss?
By classifying sensitive data and alerting on policy violations, DLP provides protective actions that can prevent users from accidentally or intentionally mishandling data. Unauthorized data use can put an organization at risk, but with monitoring, you can identify potential incidents before they have a chance to cause catastrophe.
However, there are limitations to DLP solutions, making them an asset, but not enough for an iron-clad security defense on their own. DLP relies on policies, but the policies may not work as intended based on a rigid set of controls. For example, if the program prevents users from sending PII to external drives and applications, the action would be blocked should a user tried to attach a file containing PII to an email. That email may be perfectly in line with business operations, but the user is limited based on a rigid, transactional policy.
SIEM
If your organization has a security information and event management (SIEM) system like Splunk or SolarWinds, that’s an excellent start. But a SIEM doesn’t automatically secure your organization. SIEMs are limited by configurations, cost, false positives, and required staffing. To fully use a SIEM, someone needs to monitor logs and alerts 24/7. Without a dedicated team to pull reports and observe the logs, security threats may fall through the cracks.
Certain tools integrate with other layers of defense to enhance security. To boost your security posture and reduce your technological attack surface, adding cloud-based user activity monitoring at the application layer provides additional visibility into how application users are accessing and interacting with data.
By integrating user activity monitoring with a SIEM, you can obtain information such as the IP address where an export originated and the name of the report exported. Then, you can correlate that information with the SIEM to analyze the data and findings. This reduces false positives and eliminates the need for a 24/7 monitoring staff.
Given its vulnerabilities and limitations, a SIEM solution should be just one layer of many in a defense-in-depth approach to safeguarding data.
Ensuring your organization has a robust defense-in-depth strategy
The first step to ensuring that your organization has a thorough defense-in-depth approach is to review your current security measures and evaluate their effectiveness. Consider your organization’s:
- Administrative security controls, such as policies and procedures for increased data protection.
- Physical security like keycards, access codes on locked doors, and workstation locks.
- Perimeter security, which may include anti-virus and anti-malware programs, DLP solutions, perimeter firewalls, border routers, and other boundaries between the public and private sides of a network.
- Network security such as VoIP protection, proxy content filters, remote access, and wireless security.
- Endpoint security, which secures devices accessing an organization’s network remotely or wirelessly, including device firewalls, patch management, content security, antivirus, antispyware, and host intrusion prevention systems.
- Application security, including user activity monitoring, dynamic app testing, encryption, application firewalls, database monitoring, and runtime application self-protection technology.
The most successful organizations layer multiple strata of technology and security to protect their mission-critical assets. If your organization already has one or two solutions, that may be a great start, but not enough to prevent insider threats, outside attacks, and system compromises from exposing your sensitive data. Instead, it’s vital to establish customer and employee trust, maintain compliance, and secure your mission-critical data through a defense-in-depth approach to cloud security.
