Financial Services Utilize User Activity Monitoring for Data Theft Prevention

Morgan Stanley was granted yet another restraining order against a former employee who opened an independent advisory firm and contacted former clients after several requests to return the company data. This is the fourth temporary restraining order granted to Morgan Stanley and a ruling that now allows an expedited Financial Industry Regulation Authority (FINRA) arbitration hearing.
The situation is no anomaly, but one instance of many in which departing brokers of financial services firms take client data to start their own operations or to sell it for financial gain. The losses are hefty with the cost of a data breach for financial services firms being the second highest across industries at $245 per record, and the average amount of records stolen at 28,512. It’s clear from these statistics that data theft prevention is a top priority for organizations worldwide.
Below are a few more recent instances of employee data theft in the financial services industry:
- Ex-Morgan Stanley brokers agree to plead guilty to $500k fraud scheme
- Lawyers for ex-Wells Fargo broker ordered to hand over client data
- Stolen Client Data Costs Morgan Stanley $1 Million; Broker Got Probation
Why is employee data theft so prevalent in the financial services industry? It has to do with employee perception and the high value of client data.
Do Your Employees Perceive Company Data as their Own?
Perception regarding company data is seemingly blurry for a majority of departing employees. In a study by Ponemon, 74% of respondents have access to confidential information such as customer data contact lists, employee records, financial reports, and software tools.
Among the 15% of respondents who changed or lost their jobs in the previous 12 months, 50% took confidential company data. 52% of these respondents didn’t see the use of such documents as a crime.
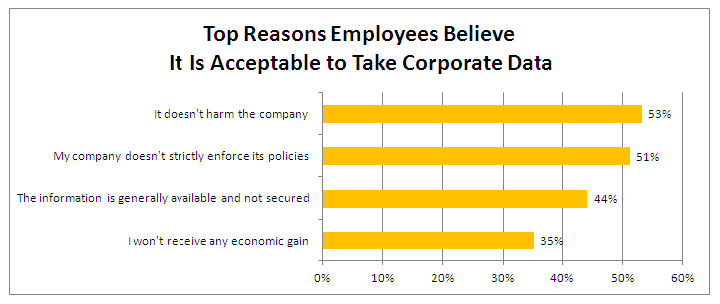
Financial services firms rely on the security of this data to maintain trust between themselves and their clients. Therefore, data theft prevention is a critical aspect of any firm’s cybersecurity program. Once the data leaves your organization, there is little that can be done besides legal action that may take months or even years to resolve.
Below are effective practices financial services firms should take to set the framework for data security and keep data out of the hands of malicious actors:
Point Your Resources in the Right Direction: Cybersecurity Risk Assessment
Firms should first conduct regularly cybersecurity risk assessments to uncover the greatest threats to their company data. Risks to company data can come from vendors, privileged user accounts, specific departments, users, or third-party contractors. Once vulnerabilities are uncovered they can be prioritized and mitigated accordingly, ensuring that resources are used in the most effective way possible.
If You Don’t Know What’s Happening You Can’t Stop It: User Activity Monitoring
Implement user activity monitoring (as recommended by FINRA) and behavioral analytics to monitor applications such as Salesforce for employee and affiliate access to sensitive data i.e. client data. This technology can be used before, during, and after the offboarding process to answer questions like:
“What are my privileged users accessing? Who’s exporting company data? Why is Jim Taylor in sales accessing more accounts than usual? Why was this new user account created? What reports are my departing employees accessing?
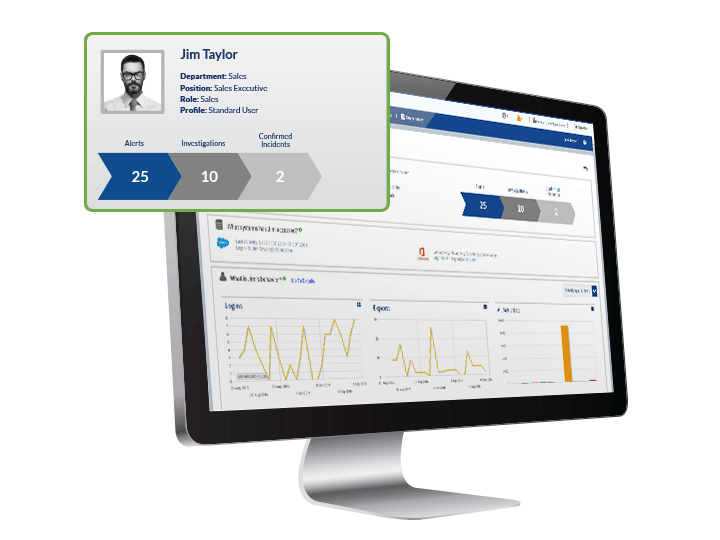
These business-critical questions and more can be addressed to detect and prevent malicious behavior before, during, and after an employee offboarding using Imprivata FairWarning for Cloud Security, all at the click of a button.
Incident Response Plan
For data theft prevention, organizations need an incident response plan in place. Once a security incident is detected, it needs to be immediately addressed and remediated. Time matters when it comes to a data breach. The Ponemon Institute cites that the average amount of time to detect a breach is 206 days, which is far too long for the damage to be done. Organizations should establish policies and procedures for escalating and responding to security incidents as quickly as possible.
Avoid Legal Action or Worse
A financial service firm’s data is, in essence, the core of their business, as it directly relates to the safety and security of their customers. To mitigate risk associated with employees who take company data outside the organization, firms need an overarching view of where the greatest risk lies. Once identified, they can establish policies, tools, and procedures to identify and prevent breaches to avoid legal action, or worse — not knowing that a breach has occurred while the data is already out the door.
