Best Practices for Avoiding False Positives for Healthcare Data Security
False positives – when an alert turns out to be a false alarm – are a frustrating thorn in the side of privacy and security officers. When alerts pile up and overwhelm your workload, it makes finding and mitigating legitimate healthcare data security incidents all the more challenging. The silver lining is that there are ways to drastically reduce false positives. But what impact do false positives have on healthcare security and how can they be avoided?
The impact of false positives is felt in lost time and important alerts slipping through the cracks. And they can be overwhelming for security officers and CISOs who are inundated with alerts where half aren’t even real incidents.
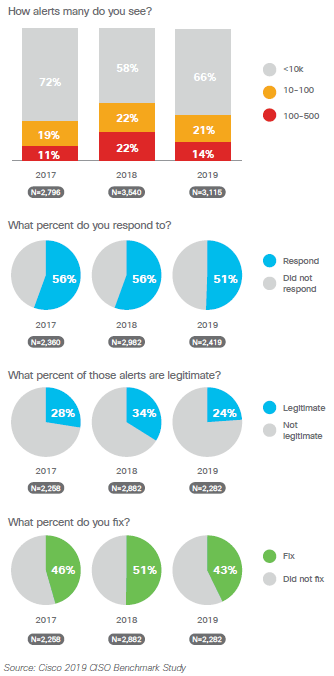
According to the 2019 Cisco CISO Benchmark Study, there has been a dramatic drop in the number of legitimate reports that get remediated compared to the previous year – from 50.5% in 2018 to 42.8% in 2019 – which means that nearly 60% of alerts that CISOs received were false positives.
While the study also found that fewer alerts occurred overall since 2018, as many as 35% of CISOs still saw between 10,000-50,000 alerts daily – and only half of those were responded to. But if even one alert is a serious threat, that opens your organization to significant cybersecurity risks.
With worrisome statistics like these, what are the best practices for reducing false positives?
Best practice: implement patient privacy monitoring
Reducing false positives is key for maintaining an effective cybersecurity posture at any organization. To accomplish this, implementing a patient privacy monitoring platform that integrates with your primary EHR can help identify and filter false positives. A full-lifecycle platform with features like behavioral correlations can automatically filter out 40-70% of false positives, dismissing business-related alerts. This increases peace of mind with the knowledge that the alerts that you receive are legitimate.
“The case has never been stronger for security threat response tools that can ingest broad data sets, provide visibility into that big data, and provide a means to rapidly take action.” – 2019 Cisco CISO Benchmark Study
Best practice: utilize AI & machine learning
While monitoring patient records for potential security incidents is vital, it can be frustrating and time consuming to analyze and dismiss a significant number of false positives. Artificial intelligence (AI) and machine learning can dramatically reduce time spent on manual efforts. Machine learning is the facet of AI that learns much like a human does by ingesting massive quantities of information, analyzing how privacy and security professionals have acted on specific types of alerts in the past, and then mimicking that behavior. In that way, AI and machine learning are excellent resources for knowing which alerts to dismiss automatically and which to send back to security officers for further investigation. This saves a substantial amount of time, allowing security professionals to focus on investigating legitimate violations.
At Stony Brook Medicine, introducing a patient privacy monitoring solution with AI and machine learning capabilities allowed their privacy and security team to cut alerts in half in a single year, providing them with the benefit of considerable time savings and allowing them to focus on high-risk patient record access only.
“Machine learning absolutely does reduce more of those false positives that we were seeing, and we have data that shows that our cases, our investigations, our alerts are cut in half since we’ve implemented AI.” – Stephanie Musso-Mantione, Chief HIPAA Privacy Officer at Stony Brook Medicine
Best practice: when it comes to vendors, less is more
Adopting security platform vendors for patient privacy monitoring and AI capabilities is an excellent way to reduce false positives. However, it is possible to have too many – the less vendors organizations have, the less alerts they will receive, and the alerts they do get are more likely to be legitimate. According to the 2019 Cisco CISO Benchmark Study, in 2018, 21% of CISOs surveyed had more than 20 vendors and 5% had more than 50. This year, those numbers have fallen to 14% and 3%, respectively. The survey also found that the fewer point solutions an organization has, the better they could manage their alerts through an enterprise architecture approach. Instead of buying and working with additional vendors, implementing a single vendor that manages the full lifecycle of healthcare data security incidents and consolidates different services into a single package is more effective at reducing false positives.
As essential as it is to monitor alerts, having a high ratio of false positives can overwhelm even the most successful CISOs and security professionals – especially when more than half of those alerts aren’t legitimate. It can be exasperating, but by implementing solutions like patient privacy monitoring, AI, and consolidating vendors, you can get a handle on your alerts and start monitoring only the highest-risk access, ensuring that no serious security incidents fall through the cracks.
