The Cost of Insider Threats in the Healthcare Industry and How to Reduce Them
From ransomware to social engineering, cybersecurity attacks plague healthcare organizations all too frequently. But the most common risk isn’t malicious actors trying to break in from the outside – more often than not, threats come from within an organization. The cost of insider threats can mount into the millions – and can lead to loss of patient trust. Shedding light on the monetary losses caused by insider breaches, Ponemon Institute has released its 2020 Cost of Insider Threats Global Report.
The study, which reaches across healthcare and other industries, surveyed 964 IT and IT security practitioners in 204 organizations across North America, Europe, the Middle East, and Asia-Pacific. The results are staggering – there has been a 31% increase in the cost of insider threats in the past two years alone, from $8.76 million in 2018 to $11.45 million in 2020. Furthermore, the number of security incidents rose by 47% within the same time period. What can organizations in the healthcare industry do to protect themselves from the growing risk that insiders pose?
This article details the types of insider threats that affect healthcare organizations, the financial impact, and best practices to safeguard patient data from risks that originate within a health system or insurance provider’s network, whether that’s through an EHR like Cerner, a CRM like Salesforce, or applications like Office 365. According to the study, there are three types of insider threats:
- The careless or negligent employee or contractor
- The criminal or malicious insider
- The credential thief (imposter risk)
The careless or negligent employee or contractor
Careless workers can be well-meaning, but negligence on their part can cost organizations millions. If an employee or contractor acts carelessly, such as leaving workstations and doors unlocked, installing unapproved applications onto company devices, or leaving sensitive personal health information (PHI) or personally identifiable information (PII) in plain sight, it can leave your organization vulnerable to a cyberattack. And negligence is the most frequently encountered insider threat, comprising 62% of all incidents caused by insiders. According to the Ponemon report, incidents caused by careless employees or contractors cost an average of $307,111 per occurrence across all industries and can add up to $4.58 million per organization.
Furthermore, careless workers are more likely to snoop on their colleagues, household members, people in their community, and high-profile patients, leading to consequences ranging from policy violations to an expensive breach that could land your organization in the news or on the Office of Civil Rights’ (OCR) “Wall of Shame.” According to the HIPAA Journal 2019 Healthcare Data Breach Report, HIPAA violations like these cost healthcare organizations $12 million in financial penalties to the OCR last year alone.
To mitigate the risk that negligent workers pose, prioritize onboarding and ongoing training so that all employees and contractors clearly understand the importance of data security and HIPAA compliance from the point of hire and onward throughout their employment. Training users carries the added benefit of informing employees, contractors, and students of action plans when an incident or breach occurs so it can be resolved more quickly and efficiently.
“Make sure that the training that you’re doing, the ongoing training in particular, is really focused on the challenges that you’re seeing, the questions you’re getting.”
– Anne Kimbol, Assistant General Counsel and Chief Privacy Officer at HITRUST
Implementing a patient privacy monitoring solution and user activity monitoring for cloud applications like Salesforce can also help prevent carelessness and promote a culture of privacy across the board by spotting improper access and trends within departments. If a specific area of the organization has a pattern of falling behind in terms of maintaining privacy and security, training can be custom-tailored so that security incidents don’t occur repeatedly.
“There are lots of different ways that you can look for insider threats. Some of them are not people doing something maliciously, but it doesn’t mean we shouldn’t stop them from doing it.”
– Ed Holmes, Chief Executive Officer at Imprivata FairWarning
The criminal or malicious insider
Criminal insiders are one of the most challenging threats to detect. Unlike negligent users, they typically act with malicious intention rather than out of carelessness. They’re already inside the network and have no roadblocks to prevent them from abusing their privileges to access private information for personal or financial gain. Although malicious incidents are widely publicized, only 23% of overall security incidents are caused by them. According to the 2020 Cost of Insider Threats Report, incidents caused by criminal and malicious insiders amass an average of $755,760 each and add up over the course of a year. On average, each organization surveyed paid $4.08 million as a result of criminal and malicious threats from within.
As difficult as it can be to detect criminal and malicious insiders, certain countermeasures can protect PHI. Limiting access so that only users who need the information to do their jobs can reach the data helps prevent unauthorized access. Programming screen locks, monitoring for suspicious activity, and restricting the use of external storage devices also minimizes the potential damage of a nefarious individual.
The credential thief (imposter risk)
Credential theft (imposter risk) is a type of cybercrime where the culprit uses tactics such as phishing, spear phishing, vishing, smishing, and social engineering to steal login information. Once the attacker gains access to an organization’s network, they share the same user privileges as their victim, gaining visibility into sensitive patient information such as names, addresses, health history, credit card information, and social security numbers.
Although imposter risk occurs in only 14% of insider threat events, incidents caused by credential theft are the most costly. In fact, the typical cost per credential theft incident is nearly triple that of negligence incidents at a staggering $871,686. Annually, incidents caused by credential thieves amount to $2.79 million, on average.
With millions of dollars and patient trust at stake, how can healthcare organizations protect themselves from imposters and credential thieves? Prioritizing security training on a regular basis can help inform users of red flags. Common signs of phishing, smishing, spear phishing, and similar attacks include:
- Emails and texts from unrecognized sources
- Emails originating from outside of an organization, even if the sender is disguised to look like they’re an employee
- Frequent typos
- An unexpected email with an embedded link or attachment
- Hyperlink text that does not match its destination when you hover your mouse over it
- Communications sent outside of business hours
- Irrelevant subject lines
- Emails that contain a link or attachment to avoid negative consequences or to offer value
These types of cyberattacks are unique because they require the user to take action by clicking a link or opening an attachment to work. Training users to detect the signs of credential theft can prevent users from taking these actions, stopping imposter risks in their tracks.
Preventing insider threats like negligent workers, malicious insiders, and credential thieves can save healthcare organizations millions. In fact, the faster an incident is contained, the less expensive it is to remediate. According to the Ponemon report, it takes an average of over two months – 77 days – to contain an insider incident across all industries. And with many points of entry for the average employee – an EHR, Salesforce, Office 365, etc. – monitoring users for suspicious activity should be a top priority.
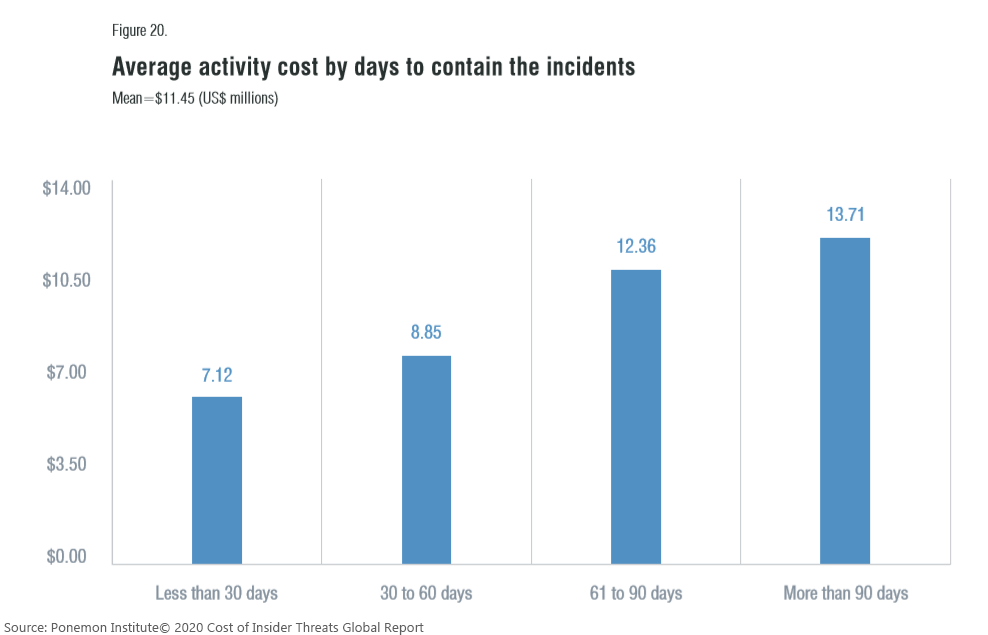
The Ponemon report also found that the longer it took to contain an insider incident, the more expensive it was. Organizations that took more than 90 days to contain an insider attack experienced the highest mitigation costs – $13.71 million in contrast to $7.12 million for systems that discovered the incident within 90 days. For the health and pharmaceutical sectors, it costs $10.81 million on average to remediate.
One of the most troubling findings of the Ponemon study is that insider threats are increasing. In the past two years, the average number of incidents involving employee or contractor negligence has increased from 13.2 to 14.5 per organization – and 60% of organizations surveyed suffered more than 30 insider incidents per year. The study determined six key factors that affect the cost of insider threats:
- Monitoring & surveillance: Taking actions to enable organizations to proactively detect violations and potential cyberattacks, including steps like installing patient privacy monitoring for EHRs or user activity monitoring for cloud applications
- Investigation: Uncovering the source of an incident as well as its scope and magnitude
- Escalation: Informing key stakeholders about incidents and organizing a response
- Incident response: Forming an incident response team and taking steps to create a final management response
- Containment: Putting a stop to – or reducing the severity of – insider attacks, including shutting down compromised applications
- Ex-post analysis: Reducing the chance that insider incidents will happen again, including steps taken to inform key stakeholders of recommendations to minimize future harm
- Remediation: Repairing affected systems and core business processes, including restoring damaged information assets and IT infrastructure
The fastest-growing cost among these activities is investigation at $103,798 per incident, with the average cost across all types of insider attacks rising 86% in only two years. And the price isn’t limited to dollar amounts – of insider-related events that carry monetary impact, direct and indirect costs can include:
- Loss of mission-critical data or intellectual property
- Downtime on productivity across an organization
- Equipment damages
- Detection and remediation costs
- Legal impact such as litigation and regulatory costs
- Loss of patient trust
- Damage to organizational reputation
In the healthcare industry in particular, insider threats can affect lives. According to a study by Vanderbilt University, hospital mortality rates, as well as the number of fatal heart attacks, rise drastically following a data breach. In fact, the research suggests that breaches cause up to 2,100 deaths per year in the United States alone.
“We’ve reached a point in the healthcare sector where the vast majority of attacks that we are seeing now have some kind of impact on patient safety.”
– Iliana Peters, Shareholder at Polsinelli and former Acting Deputy Director of the OCR
To protect your organization from insider threats, understanding risk factors is vital. Five signs your organization is susceptible for insider threats are:
- Users that aren’t trained on laws and regulations related to their work and affect the organization’s security
- Users that don’t know the steps to take to secure the devices they use, whether that is company technology or devices they bring that access the company’s database
- Users that send confidential data to unsecured cloud locations, leaving organizations wide open to risk
- Users that break security policies in order to make tasks easier
- Users that fail to keep devices and software upgraded and patched to the latest versions
With insider threats on the rise, healthcare organizations must protect themselves against the risks that they pose to save both costs and patient lives. By onboarding new hires and continuously training them on HIPAA requirements, best practices for cybersecurity, as well as potential consequences for legal and policy violations, users will be empowered with the knowledge needed to protect the privacy and security of PHI, PII, and other sensitive information. And strengthening cybersecurity measures along with implementing proactive patient privacy monitoring for EHRs and user activity monitoring for cloud applications like Salesforce can stop attackers in their tracks – before they can walk away with valuable information.